Vector and Splunk
Splunk is a software platform used for searching, monitoring, and analyzing machine-generated data. It is commonly used in ICE Servers to stream logs into Splunk for advanced log analysis and monitoring.
To configure Vector logging via Splunk
1. Install Docker
Ensure Docker is installed on your system. The following commands can be used to install Docker on Ubuntu:
sudo apt -y update
sudo apt -y install apt-transport-https ca-certificates curl software-properties-common
curl -fsSL https://download.docker.com/linux/ubuntu/gpg | sudo apt-key add -
sudo add-apt-repository "deb [arch=amd64] https://download.docker.com/linux/ubuntu $(lsb_release -cs) stable"
sudo apt -y update
sudo apt -y install docker-ce
2. Configure Vector
Update your Vector configuration to use the splunk_hec_logs sink. The following example configuration is provided in YAML format:
sinks:
my_splunk_hec_logs_sink:
type: splunk_hec_logs
inputs:
- my-source-or-transform-id
endpoint: https://http-inputs-hec.splunkcloud.com
host_key: hostname
indexed_fields:
- field1
compression: none
default_token: ${SPLUNK_HEC_TOKEN}
encoding:
codec: jsonRun Vector
3. Configure a Vector Agent for Splunk HEC Logs on ICE OS
Ensure that the Vector agent is running and configured to send logs to the Splunk HTTP Event Collector (HEC).
Note: For optimal performance, set up a different data source for each ICE Server or ICE Server Geo setup.
A. In the ICE OS Configuration Wizard, click the External Log Store tab.
B. Ensure Install Vector Agent is selected.
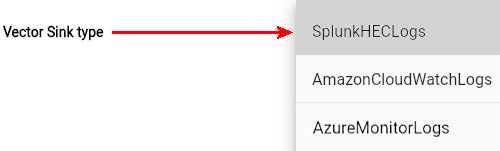
C. Select the SplunkHECLogs Vector Sink Type.

D. In Endpoint, enter the URL to the Splunk HEC server you are using. For example, https://splunk.mysite.app:8080.
E. In Endpoint Port, enter the port used for this connection. The default port is 8088.
F. In Access Token, paste the access token acquired from the Splunk server.
G. Click the Apply button. The logs from ICE Server are now streaming into Splunk. Note that a few minutes delay is not uncommon before log messages are streamed into Splunk logs.
Note: You can also configure a Vector Agent for Splunk HEC logs via commands. Vector’s online documentation provides detailed instructions on configuring the Splunk HEC logs. See Splunk HTTP Event Collector (HEC).
Ensure you update your Vector configuration to accommodate the name change from splunk_hec to splunk_hec_logs.
The following example shows a configuration for Splunk HEC logs in YAML format:
sinks:
my_splunk_hec_logs_sink:
type: splunk_hec_logs
inputs: ["my-source-or-transform-id"]
endpoint: "https://http-inputs-hec.splunkcloud.com"
host_key: "hostname"
indexed_fields: ["field1"]
compression: "none"
default_token: "${SPLUNK_HEC_TOKEN}"
encoding:
codec: "json"
4. Verify Log Reception
Check the Splunk interface to verify that logs are being received correctly. Navigate to the appropriate log group and check for incoming log entries. You can also use the following curl command to test the configuration:
You should see a response similar to {"text":"Success","code":0} indicating that the logs are being received by Splunk.