Using ICE-Generated Certificates
This option creates a 12-month self-signed TLS certificate and assigns it to the ICE Server for use in securing HTTPS connections. The RTS certstores generated by the configuration wizard cannot be downloaded. Connecting a Tactical component requires the generation of your own RTS Certstores and their installation. For instructions see Creating a Certstore in the ICE Admin Guide.
Note: Federation requires manual creation of a certstore that is uploaded to the systems after installation or upgrade. Optionally, organizational certs valid with FIPS requirements are also supported.
To use an ICE-Generated Self-Signed Certificate Authority (CA)
1. Select Enable TLS to activate the fields for creating a TLS certstore and/or uploading certificates.

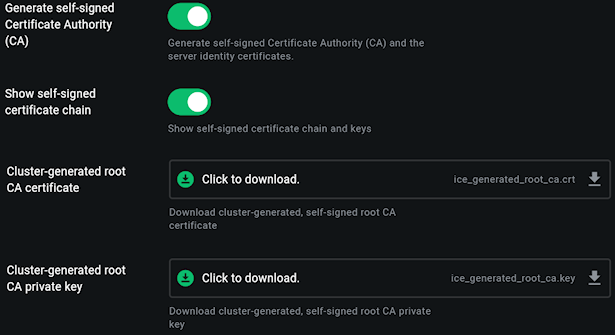
2. Select Generate Self-Signed Certificate Authority (CA).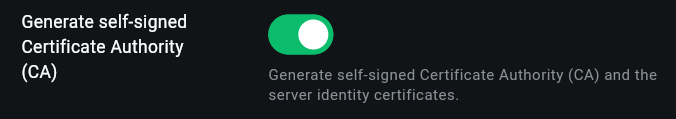

3. Open Status and wait for Node Status to turn green
4. Click Apply.
You will be notified if the keys are successfully provisioned.
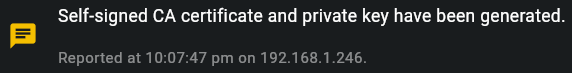
You will be notified if the keys are successfully provisioned.

5. In Cluster Ingress Hostname, enter the Ingress FQDN. This address must be resolvable on the DNS. If your ICE Server has multiple Ingress Hostnames, then enter them one at a time on a separate line.
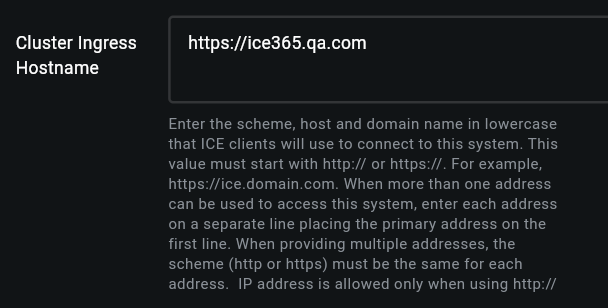
Click Apply and continue to the Server tab instructions.

Click Apply and continue to the Server tab instructions.
Note: You can download the root CA certificate and private key for use as needed by activating Show Self-Signed Certificate Chain.